Blessing or Bane: Third-Party Vendors
In today’s interconnected business environment, organisations rely heavily on external IT vendors to support operations. While these partnerships offer efficiency and cost-effectiveness, they also introduce significant risk - particularly around cybersecurity and data protection. At the recent “Blessing or Bane: Third-Party Vendors” webinar, Wong Onn Chee, CEO of Rajah & Tann Cybersecurity Private Limited and Technical Director of Rajah & Tann Technologies Private Limited, provided valuable insights on managing these risks and shared real-world case studies highlighting the consequences of weak third-party risk management.
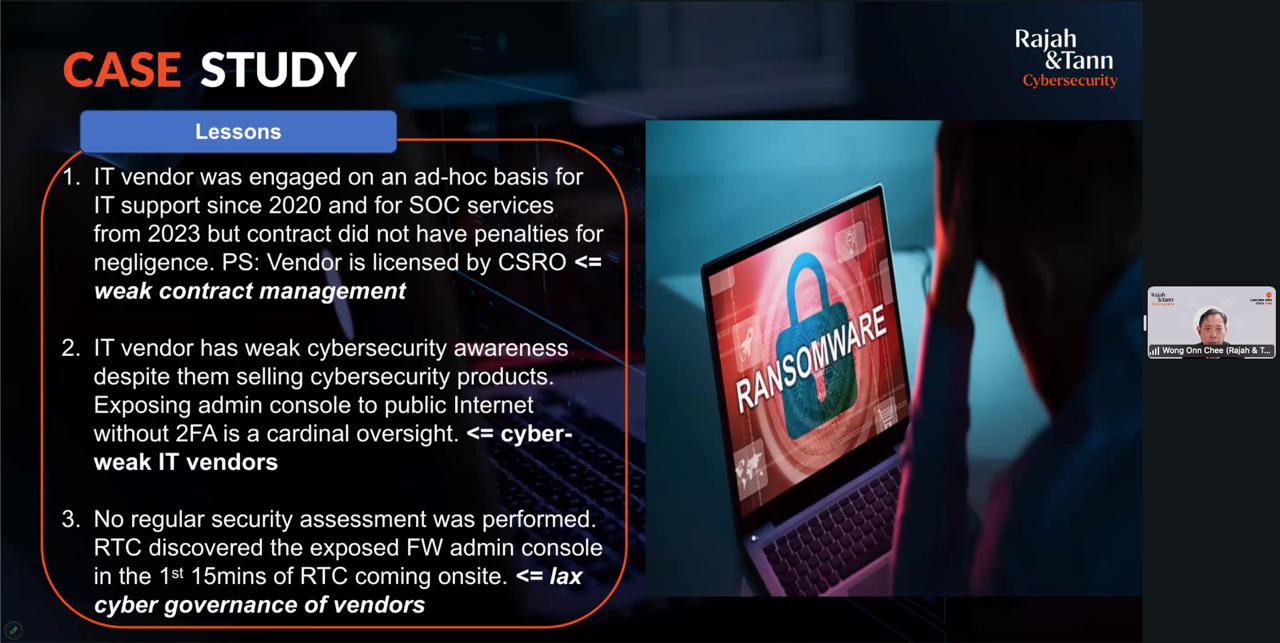
A key takeaway from the session was that organisations must ensure that third-party vendors have comprehensive incident response protocols in place. Some vendors may only offer limited support during security incidents, which can leave critical systems exposed once predefined support hours are exhausted. This gap increases the risk of regulatory breaches and financial penalties if incidents are not properly managed or remediated.
Another issue discussed was the lack of transparency in service contracts. To remain cost-competitive, some vendors exclude essential cybersecurity measures, such as forensic imaging of critical servers or endpoints. Without this process, organisations may face challenges in conducting thorough investigations when security incidents occur, leading to delays in containment and regulatory reporting.
The absence of local expertise was also highlighted as a significant risk. Vendors without a physical presence in Singapore or familiarity with local regulations may struggle to meet compliance expectations set by authorities such as the Personal Data Protection Commission Singapore, the Monetary Authority of Singapore, and the Ministry of Health. This can pose difficulties for organisations that require vendors to engage directly with regulators, particularly in situations where face-to-face discussions are necessary.
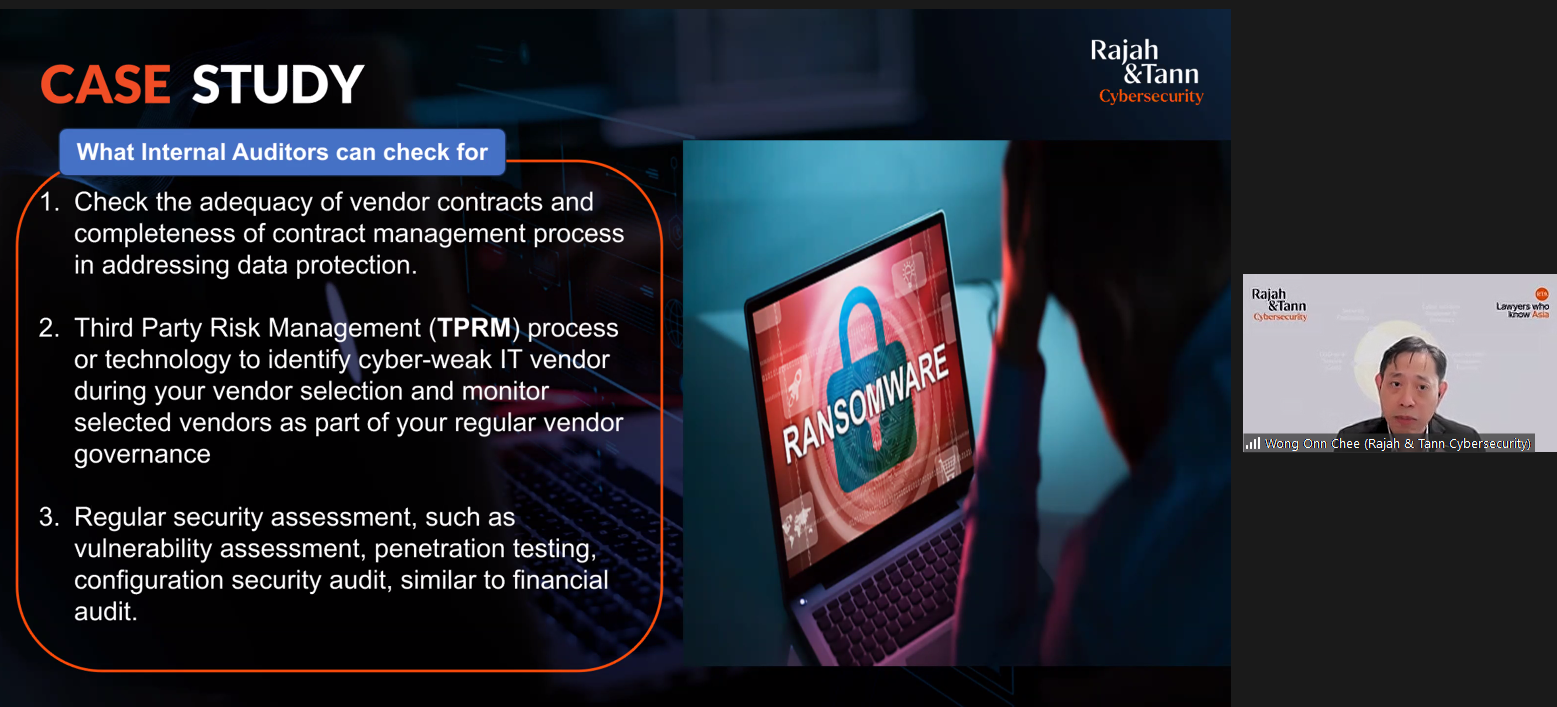
To manage third-party risks effectively, organisations should ensure that vendor contracts and contract management processes adequately address data protection requirements. A robust Third-Party Risk Management framework can help identify IT vendors with cyber vulnerabilities during selection and facilitate ongoing monitoring as part of regular vendor governance. Conducting regular security assessments, such as vulnerability assessments, penetration testing, and configuration security audits, is also essential. Just as financial audits ensure financial integrity, these security evaluations help safeguard sensitive data and maintain compliance with regulatory expectations.
The insights shared during the session underscored the importance of vigilance and proactive risk management in protecting sensitive data and ensuring compliance with local regulations. Internal audit plays an vital role in evaluating these processes and providing assurance that third-party risks are being effectively managed. By embedding regular reviews and assessments into their vendor governance programmes, organisations can enhance their ability to safeguard sensitive information and minimise the risks associated with third-party vendors.